SUMMARY
Upstream’s security lab, Secure-D, has unveiled that popular video Android application VidMate, with over 500 million downloads, triggers suspicious background activity. A hidden component within the app delivers invisible ads, generates fake clicks and purchases, installs other suspicious apps without consent and collects personal users’ information. Consequently, it depletes users’ data allowance and brings unwanted charges.
UNVEILING THE INVESTIGATION
Over a recent period, Secure-D, detected and blocked more than 128 million suspicious mobile transactions initiated by VidMate. These transactions originated from 4.8 million unique mobile devices across 15 countries.
If not blocked, they would have subscribed users to premium digital services potentially costing them up to $170 million in unwanted charges.
VidMate is a popular Android app that allows users to stream and download videos and songs from services such as Dailymotion, Vimeo and YouTube. VidMate is not available on Google Play store but can be downloaded through third-party app stores like CNET or Uptodown. According to publicly available information, VidMate was developed by a subsidiary of UC Web, which is owned by Chinese conglomerate Alibaba.
INVESTIGATION PROCESS & FINDINGS
SETTING UP THE INVESTIGATION
Secure-D recorded a high number of suspicious transactions across multiple countries originating from VidMate. This was cross checked with reports from multiple users noting their handsets were performing non-user initiated subscriptions to digital services leading to unwanted airtime charges. We purchased three of these devices from their owners and placed them in our lab for investigation. All users confirmed their phone was “acting up” with problems such as unexpected data use, overheating and reduced battery even when the device was not in use. The handsets were a Huawei ALE-21, an LG G5 H850 and a Sony G3311.
All handsets had the VidMate application installed, presenting an opportunity to check and confirm it was the common factor. The testing involved operating the device while isolating it in a sandbox environment to examine all HTTP traffic into and out of the device and reveal anything amiss.
THE ALARMING FINDINGS: VIDMATE’S SUSPICIOUS BEHAVIOR
During the testing, each handset carried out the suspicious activity associated with VidMate, allowing the Secure-D team to isolate and examine the relevant traffic.
Upon download, the app already contains an inactive and hidden suspicious code. Once active on the device Vidmate loads this 3rd party SDK called Mango and executes it.
In turn, Mango communicated with a command and control server that issued instructions for delivering invisible ads to the mobile device and simulating clicks to access and confirm paid subscriptions. Although these views and clicks were reported as genuine to the ad networks, the activity took place in the background and wasn’t visible to the end user. At the time of the investigation (March 2019), the app also started collecting personal user information such as International Mobile Equipment Identity (IMEI), International Mobile Subscriber Identity (IMSI) or IP address, without requiring user permission, and transferring them to servers in Singapore owned by Nonolive (http://nonolive.com/), an Alibaba funded company, according to publicly available information.
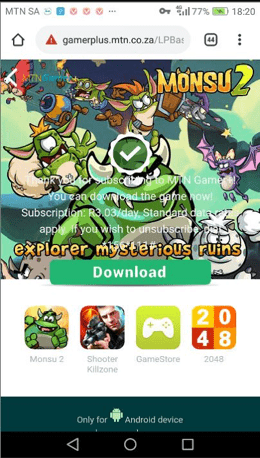
The in-depth analysis revealed that Mango began encrypted connections with the domains sty.zkmobi.com and online.hoversnake.com:1688. These connections led the device to make continuous requests to online ad servers and access landing pages where the phone attempted to “sign up” to digital subscriptions. One out of the many cases during the testing was one mobile device that made a successful subscription attempt through the host gamerplus.mtn.co.za.
The sequence flow of the encrypted requests that led to this landing page is the following:
1. http://q-mobi.go2affise.com/click?pid=71&offer_id=1815671&sub1=1550710759520010291
2. http://ngdfx.com/WNedFFsJy?offer=11191&sub1=5c6df9caaf7c0a0001690d47&sub2=71
3. http://ad.efungame.net/jshyad/getad?adid=3509¶id=4145&oliclick=05g6tehqt6qfj98
4. http://ptldynamic-gamerplus.mtn.co.za/0001vU?payid=190221WAkuxVN76jIEV3TesgCu¶id=4145
5. http://gamerplus.mtn.co.za/LPBase/tok528/, which is the landing page on which the suspicious subscription took place. This page contains the “Join Now” button, which completes the subscription of a user.

6. http://gamerplus.mtn.co.za/LPBase/tok528/subscribe?path=success&locale=en, which presents the “Thank you” page after the successful subscription.
The code used was intentionally obfuscated to deter reverse engineering that might reveal its true nature. This obfuscation included code minification (removing all characters not strictly required for functionality) and string encryption that had no obvious security benefit.
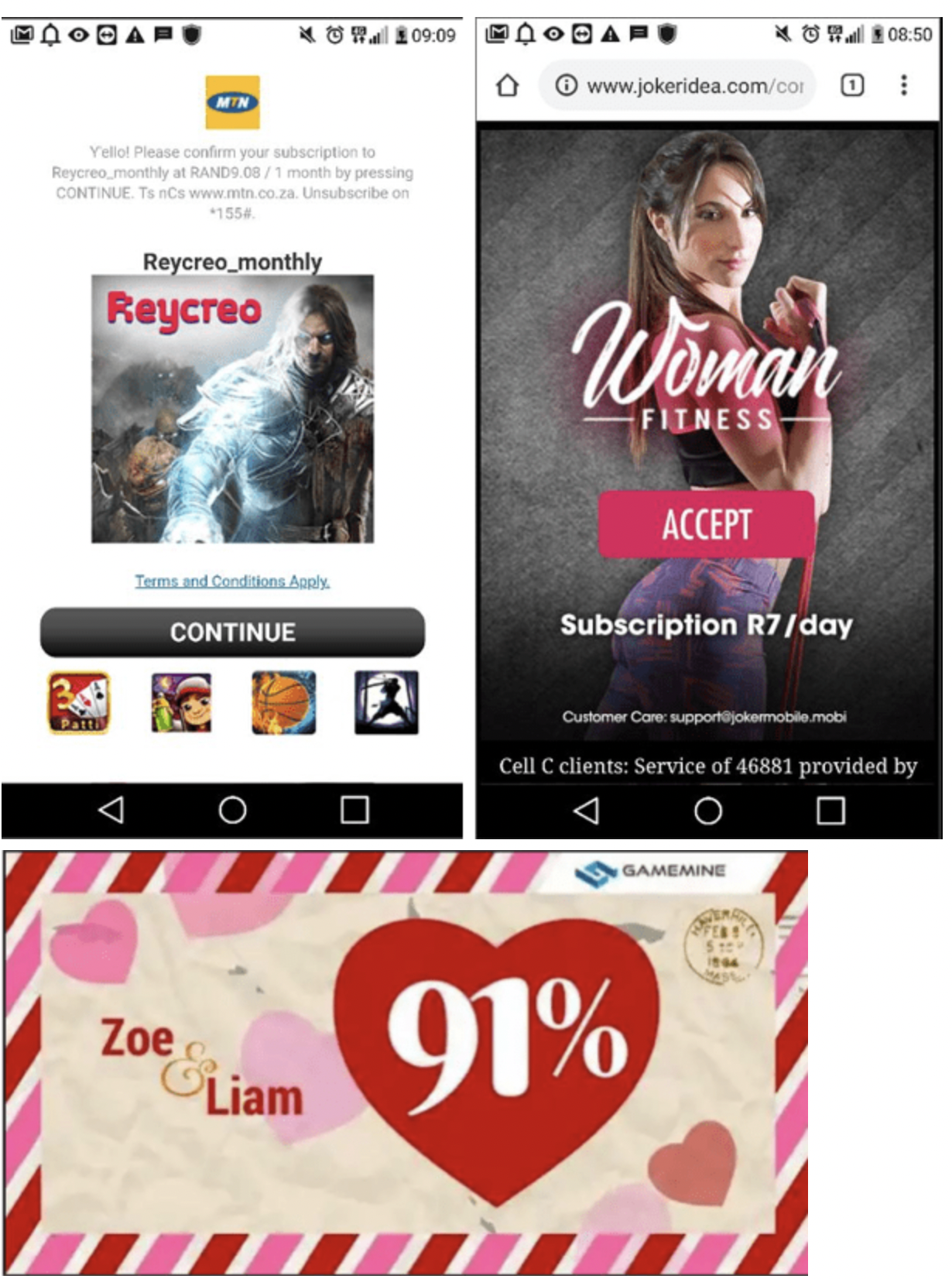
Examples of such ad network pages and ad banners loaded by the app in the background and are completely invisible to the user:
HOW VIDMATE ABUSES PERMISSIONS
Based on the AndroidManifest.xml of VidMate it was clearly determined that the application requests excessive permissions that a normal video player and downloader does not need. These include downloading and installing other software without user consent, which Secure-D’s investigation showed the app is indeed doing.
Some examples of suspicious permissions are:
| Permission | What it allows |
| android.permission.SYSTEM_ALERT_WINDOW | Allows the application to create windows shown on top of all other, making it a very dangerous permission. |
| android.permission.REQUEST_INSTALL_PACKAGES/ android.permission.DOWNLOAD_WITHOUT_NOTIFICATION |
Allows the application to install and download other unknown apps without the user’s knowledge or permission. |
| android.permission.WRITE_SETTINGS | Allows the application to read or write system settings. |
| android.permission.READ_LOGS | Allows the application to access the user’s device log files, which can contain user’s sensitive information. |
SCALE & IMPACT
Secure-D blocked more than 128 million attempted mobile transactions initiated by VidMate across 4.8 million unique devices and if not blocked would have totalled up to $170 million in unwanted premium charges.
Most of the suspicious activity, which is still ongoing, was largely centered in 15 countries. 43 million of the suspicious transactions flagged by Secure-D are coming from devices in Egypt, 27 million from Myanmar, 21 million from Brazil, 10 million from Qatar, and 8 million from South Africa. Among the top affected markets are also Ethiopia, Nigeria, Malaysia and Kuwait. These are countries where digital payments via mobile airtime are common and often the only way to make financial transactions, as most people are unbanked.
The Secure-D lab tests also revealed that VidMate consumes significant battery life and bandwidth, eating up more than 3GB of data per month. That could add up to users paying $100 a year in mobile data charges. In markets such as Brazil, this represents nearly half a month’s work paid at minimum wage.
CONCLUSIONS, EFFECTS ON USERS & MITIGATION
VidMate’s advertised purpose and features disguise systematic suspicious activity in the background including fake ad views and attempted digital purchases. While the activity is partly targeted at advertisers, it affects users in the following ways:
- Increased data usage through the unseen background activity. Our lab tests showed that VidMate eats up more than 3GB of data per month per user.
- Unwanted and unexpected airtime charges for premium digital services.
- Increased battery usage leading to overheating and other performance issues.
- Last, but not least, the app -as seen at the time of the investigation- also collects personal user information and transfers them to servers in Singapore, belonging to Nonolive, a China-based company funded by Alibaba, as per publicly available information. This personal user data may include the International Mobile Equipment Identity (IMEI), the International Mobile Subscriber Identity (IMSI) or the user’s IP address.
If you are an Android user and have downloaded a suspicious app, look out for any of the above signs of infection. Deleting the app should remedy these issues. You can do it by following the simple steps below:
STEP 1
Open the Settings menu of your device
STEP 2
Tap on My apps & games
STEP 3
Navigate to the Installed section
STEP 4
Tap on Vidmate (you may need to scroll to find it)
STEP 5
Tap Uninstall
VidMate is a reminder of the serious dangers of installing software from sources other than the official Google Play Store. The financial and privacy risks of letting misleading and abusive apps onto your device are simply not worth it.
FOR MOBILE NETWORK OPERATORS, CONTENT PROVIDERS & AGGREGATORS, CLIENTS OF SECURE-D
Secure-D has been blocking all suspicious activity by VidMate since its onset.
FOR INFORMATION SECURITY EXPERTS
Secure-D shares its findings with the community to help combat fraud and eliminate online threats. To request the infected VidMate APK, the complete technical analysis, a list of infected apps, security professionals can contact info@secure-d.io
Secure-D has worked with BuzzFeed News to bring this story to light. You can read their write up here.

