Upstream’s security platform Secure-D has detected and blocked more than 70 million suspicious mobile transaction requests coming from the Android app Snaptube in just six months. Snaptube has been delivering invisible ads, generating non-human clicks and purchases, then reporting them as real views, clicks and conversions to the advertising networks that serve them. The ads are hidden from users as they do not appear on-screen.
UNVEILING THE INVESTIGATION
Secure-D recorded a high number of suspicious transactions originating from Snaptube, a popular Android app available for download from third-party app stores. More than 70m suspicious transaction requests have been blocked by Secure-D originating from 4.4m unique devices in just six months.
If not blocked, those 70m transaction requests would have triggered the purchase of premium digital services, potentially costing users up to $91 million in unwanted premium charges. Most of the suspicious activity, which is still on-going, originated from devices in Egypt, Brazil, Sri Lanka, South Africa, and Malaysia.
ABOUT THE APP
Snaptube is a video downloading app for Android that launched in November 2014. The app allows users to download videos and audio files from popular video and music streaming sites, and even social networking apps. It has been developed by China-based Mobiuspace, founded in 2016, a company that has secured series B financing from Chinese VCs. There are several Mobiuspace apps available in Google Play under different developer accounts:
• https://play.google.com/store/apps/details?id=com.dywx.game.mobiuspace
• https://play.google.com/store/apps/developer?id=Mobiuspace+Tech+Top+Player
• https://play.google.com/store/apps/developer?id=Mobiuspace+Browser
Snaptube is available from third-party app stores like Uptodown.com, Aptoide.com, and UC 9Apps and according to its developer claims 40m users.
LAUNCHING THE INVESTIGATION
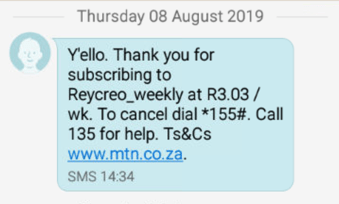
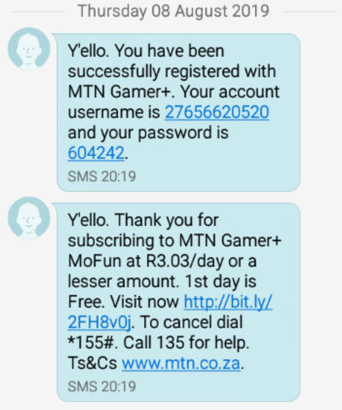
The extremely huge volumes of suspicious transactions originating in multiple countries coming from the same Android application caught the attention of Secure-D researchers. The Secure-D team examined two Android devices with the Snaptube app already installed. The devices were a Samsung SM-J120F and a Huawei WS-LX1. Researchers observed subscription verification SMS messages being sent to the infected devices, following attempts to initiate purchase of subscription to new mobile services where no user action had taken place.
WHAT SECURE-D RESEARCHERS UNCOVERED
Using the unwanted subscription confirmation messages as a starting point, Secure-D investigated further the infected devices for traces of the user requests that prompted the unwanted subscription purchases.
The infected devices were placed in a secure sandbox environment to detect and record all network traffic. Static and behavioural analysis showed that Snaptube was communicating with a command and control (C&C) server in order to identify subscription services, then attempting to subscribe the end-user to those services. The returned data is encrypted and compressed using the gzip algorithm.
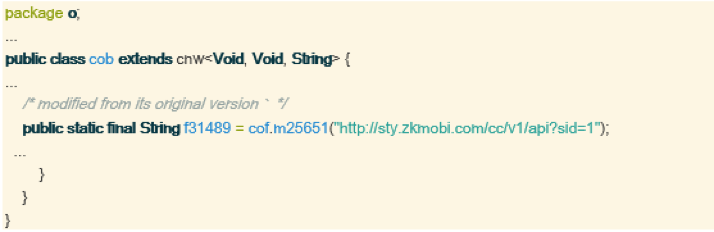
The Snaptube application on the infected devices was found to contain SDK frameworks with obfuscated hardcoded strings related to advertising services. The suspicious SDKs identified included the following:
• com.mgo
• com. mobi
• ‘o’
The SDK ‘o’ would communicate periodically with the C&C server to retrieve advertisement offers. These offers were retrieved as JSON Objects. Some objects contained the offer’s URL, along with JavaScript code that could be triggered to perform automated clicks.
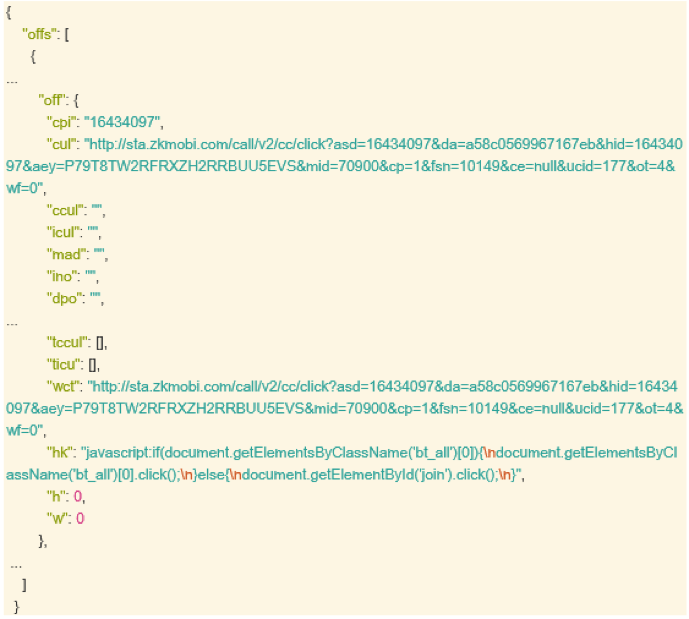
Analysis of HTTP traffic logs in the infected devices showed that all of the unwanted subscription attempts Secure-D researchers noted were initiated by the ‘o’ SDK. This observation was based on the following.
1)The root hosts from which the chain of redirections that led to the unwanted subscription started were fetched as offer URLs from the C&C server. Subsequently, an HTTP GET Request to the URL initiated the following chain of redirections:
• sta.zkmobi.com api.bdisl.com
• api.bdisl.com atracking-auto.appflood.com
• atracking-auto.appflood.com go-rilla.offerstrack.net
• [go-rilla.offerstrack.net top.ourbestcontent.com
• top.ourbestcontent.com za.reycreo.com
• za.reycreo.com 196.11.240.222
• 196.11.240.222 196.11.240.222
Finally, the successful subscription was captured in the following url:
http://za.reycreo.com/thankyoumtnza.html?result=0&resultDescription=The+user+has+been+successfully+subscribed+to+the+service.+Expect+a+datasync+for+the+same.&MSISDN=27656620520&transactionId=011000003721908081234256256776
Another example of a landing page loaded by the app in the background and completely invisible to the user follows:

2) The JavaScript code fetched with the offer URLs could execute successful subscription sign-ups when applied to the subscription service’s landing page.
The traffic which led to the unwanted subscriptions originated from the Snaptube application. Evidence for this included the following:
• The SDK ‘o’ was observed downloading additional JavaScript code used to perform automated clicks. The code was contained in a JavaScript file named global_d201805241555.js, and downloaded from the server cdn.zkmobi.com.
• The ‘o’ SDK contained code that injects JavaScript snippets performing automated clicks to the WebViews where advertised services are loaded.
• The JavaScript code used to perform automated clicks was found in the shared_prefs folder of the Snaptube application in an XML file used by the ‘o’ SDK.
• The devices were not otherwise compromised, meaning there was no other application exhibiting adverse or overly-privileged behaviour. The likelihood of malware (i.e. code unrelated to Snaptube) acting on behalf of other applications was minimal.
LINKS TO PREVIOUS BREACHES
The Mango SDK (com.mgo) found in the Snaptube app examined by Secure-D was also discovered in a previous investigation of mobile app Vidmate. Secure-D researchers also encountered a common traffic pattern and similar URLs and domains being involved as those reported with Vidmate. What is worth mentioning is that the suspicious activity from Snaptube ceased soon after the publication of a media report about the Vidmate compromise.
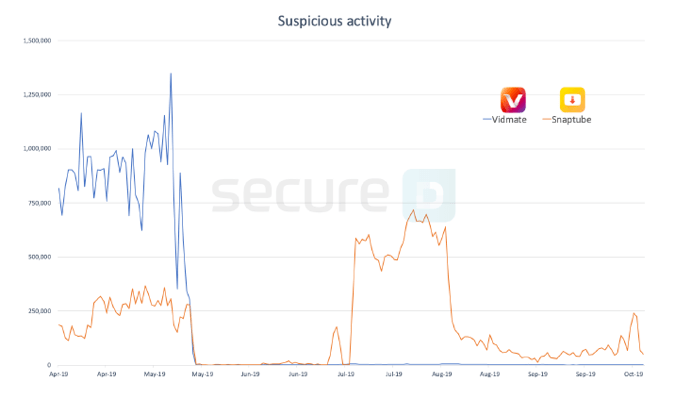
Finally, the suspicious SDKs found in both Vidmate and 4Shared were seen communicating with zkmobi.com – just as the ‘o’ SDK in Snaptube would do.
MOBILE APPS A GROWING TARGET FOR CYBERCRIMINALS- CONSEQUENCES FOR END USERS
The compromised Snaptube application analyzed by Secure-D could have enrolled end-users in unwanted mobile subscription services that cost money and consume mobile data, adding charges that eat into pre-paid airtime. In many emerging markets, using pre-paid airtime is the only way to pay for digital services.
Compromised mobile apps and mobile ad fraud remains a rising issue that affects everyone. To avoid falling victim to unwanted purchases or lose pre-paid credit, Android users, in particular, should check their phones to see if they have any suspicious apps installed. If so, they should uninstall them immediately and review any new mobile airtime charges for possible fraud.
Third-party app stores often apply less scrutiny for adverse code and odd behavior in listed applications, but even apps from official sources like Google Play can be compromised. Before any installation, users should check the app’s reviews, developer details, and list of requested permissions, making sure that they all relate to the app’s stated purpose.
FOR MOBILE NETWORK OPERATORS, CONTENT PROVIDERS & AGGREGATORS, CLIENTS OF SECURE-D
Secure-D has been blocking all suspicious activity by Snaptube since the start of its investigation.
FOR INFORMATION SECURITY EXPERTS
Secure-D shares its findings with the community to help combat fraud and eliminate online threats. To request a complete technical analysis of the Snaptube infection or a list of infected apps, security professionals can contact info@secure-d.io.

