More than 114 million suspicious mobile transactions initiated by 4shared recently blocked by Upstream’s Security Platform in 17 countries
4shared delivers invisible ads to mobile devices, incurs unwanted charges
London, July 3rd, 2019 – Upstream, a leading mobile technology company, reports that high-ranking Android application 4shared with over 100 million downloads was found to trigger suspicious background activity. The app delivers invisible ads to the device, generates fake clicks and carries out purchases of premium digital services, while reporting real views, clicks and purchases to the ad networks.
Over a recent period, Upstream’s security platform, Secure-D, detected and blocked more than 114 million suspicious mobile transactions initiated by 4shared. These transactions originated from 2 million unique mobile devices across 17 countries. If not blocked, they would have subscribed users to premium digital services potentially costing them up to $150m in unwanted charges. Most of the suspicious activity, which is still ongoing, was mostly centered in Brazil while other top affected markets include Indonesia and Malaysia.
Guy Krief, CEO of Upstream, commented: “The growing sophistication of disguised malware in the form of seemingly benign and quite often very popular applications together with the scale of the issue can no longer be ignored. No entity in the mobile ecosystem remains unaffected. From app developers, ad networks and publishers, to advertisers malware is putting a dent in both their credibility and earnings. Mobile operators, more often than not, are taking the blame while consumers not only remain widely unprotected and unwarned but are called to foot the bill. Mobile ad fraud, a $40 billion industry, will reign unchallenged unless increased mobile security rises up in the industry’s priority list”.
4shared is a popular and highly-ranked Android application that allows users to store and share video and audio files. The app generated over 100 million downloads from Google Play and ranked second in its category in Austria, 7th in Italy, and 10th in Switzerland. On 17th of April 2019, it was abruptly removed from Google Play, then replaced the following day. The new version has been submitted as an entirely new app – not a version update –keeping the original 4shared icon. As of June 21st, there have been more than 5 million installs of the ‘new’ 4shared on Google Play, free from the code responsible for the suspicious activity, unlike the more than 100 million previous app users that remained affected. 4shared is developed by Ukrainian firm New IT Solutions Ltd.
The Secure-D investigation found that 4shared contains Software Development Kits (SDKs) with embedded and obfuscated hard-coded links to Command & Control servers that access online ads via a series of redirections. They then download and load a JavaScript file that triggers automated clicks and sets cookies in order to determine whether a “click” has already been made for a specific ad in the past. The application also sends personal data to a number of servers located in the British Virgin Islands and the United States upon user consent.
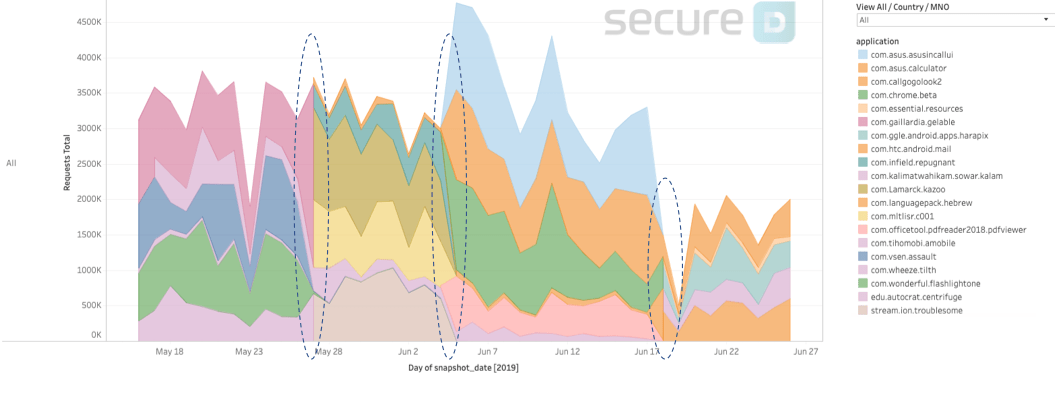
Continuing to monitor the activity of 4shared in June, Secure-D has uncovered that the app is attempting to mask its identity whilst conducting suspicious activity. Instead of appearing under its own name, it assumes the names of either existing legitimate apps (like com.chrome.beta – the new beta version of Google’s Chrome browser) or non-existing ones. The app seems to be using multiple fake names at the same time which it regularly and simultaneously changes (see graph below).
Daily activity of fake app names used by 4shared (Source: Secure-D)
4shared is only one single case; Secure-D detects more than 170 new malicious apps every day. With the mission to combat mobile fraud, protect subscribers and safeguard mobile operators, Secure-D is building the trust of mobile users – much needed in emerging markets- and supports them in becoming fully engaged participants in the data era.
For the full report on the investigation & further resources please click here
Upstream has worked with TechCrunch to bring this story to light. You can read their write-up here
###
For more information please contact:
Upstream Corporate Communications
Ε: corp.comms@upstreamsystems.com